The Microsoft Security Blog post “Defending against evolving identity attack techniques” by Igor Sakhnov, Corporate VP and Deputy CISO for Identity, outlines the latest tactics used by threat actors to compromise cloud identities and offers actionable defenses. Here’s a detailed summary based on the blog and supporting internal resources:
Key Threat Trends
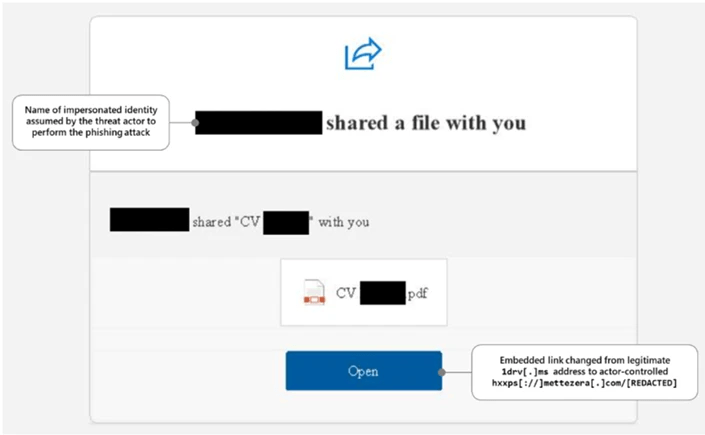
- Adversary-in-the-Middle (AiTM) Phishing: As multifactor authentication (MFA) becomes more common, attackers are shifting to AiTM techniques. These involve proxying login sessions to steal session tokens, bypassing MFA entirely. Tools like Evilginx are increasingly used by actors such as Storm-0485 and Star Blizzard.
- Phishing-as-a-Service (PhaaS): Platforms now offer ready-made phishing kits that enable even low-skill attackers to launch sophisticated AiTM campaigns.
- Social Engineering: Despite technical advances, human manipulation remains a core tactic. Attackers use lures like fake document shares or payment notices to prompt users to act quickly.
Defensive Strategies
- Phishing-Resistant Authentication: Microsoft recommends adopting passwordless solutions like passkeys and FIDO2 security keys to mitigate AiTM and credential phishing.
- Zero Trust Architecture: Internal files such as Microsoft Cybersecurity Reference Architectures (MCRA) – April 2025 and Microsoft-DefenderXDR-Overview emphasize Zero Trust principles—assuming breach, verifying explicitly, and using least privilege access.
- Identity as the New Perimeter: With 80% of breaches involving stolen credentials, identity protection is now the first line of defense. This is reinforced across multiple internal decks like FY25Q3 Microsoft-Defender-XDR-customer-deck and Module 07 – Microsoft Defender XDR.
- Continuous Monitoring and AI-Driven Detection: Tools like Microsoft Defender for Identity and Microsoft 365 Defender are highlighted for their ability to detect lateral movement, compromised users, and suspicious behavior across hybrid environments.
Actionable Recommendations
- Retire passwords in favor of phishing-resistant methods.
- Block legacy authentication protocols.
- Centralize identity management and enforce MFA for all users, especially admins and developers.
- Monitor for suspicious usage patterns and enforce least privilege access.
Microsoft’s blog post “Defending against evolving identity attack techniques” emphasizes that as attackers adopt advanced phishing and token theft methods, organizations must shift to phishing-resistant authentication, enforce Zero Trust principles, and treat identity as the new security perimeter.
For more detailed information including screenshots please review the blog HERE

You must be logged in to post a comment.